Access control lists (ACLs) are a crucial component of network security, providing a way to control and restrict access to resources based on user permissions. In simple terms, ACLs serve as virtual gatekeepers, allowing or denying access to specific networks, systems, or applications. They are an essential part of any organization’s security strategy, as they help protect sensitive data and prevent unauthorized access.
In this comprehensive guide, we will delve into the world of access control lists, exploring what they are, how they work, and why they are essential. We will also discuss different types of ACLs and their use cases, best practices for implementing and maintaining them, and the benefits they offer to organizations. So, let’s dive in and gain a thorough understanding of access control lists.
Understanding Access Control Lists (ACLs)
What are Access Control Lists?
In the world of network security, access control lists (ACLs) are a set of rules that allow or deny access to a specific resource based on predefined criteria. These rules are applied at various points within a network, such as routers, switches, firewalls, and servers. ACLs essentially act as virtual barriers, controlling the flow of traffic between different networks, systems, or applications.
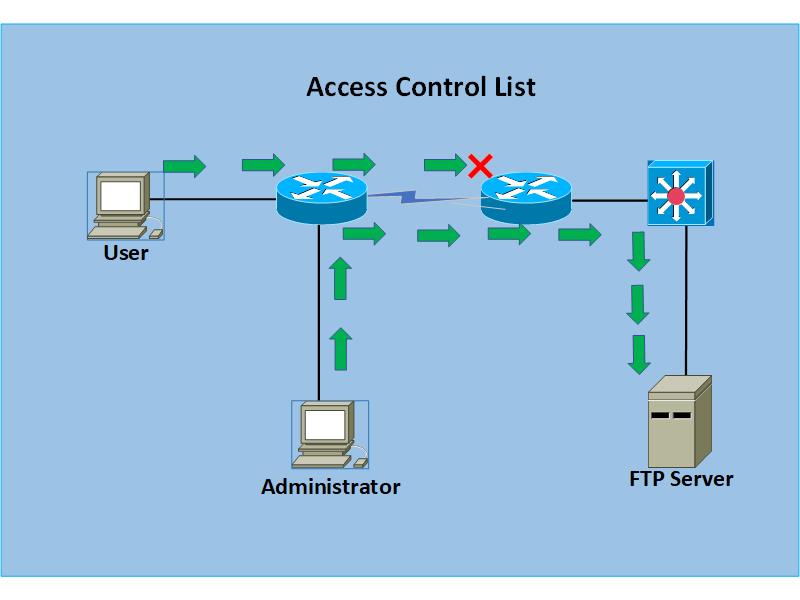
In network security, access control lists (ACLs) consist of rules that determine whether access to a particular resource is permitted or denied based on predefined criteria
An ACL is composed of two main components: an access control entry (ACE) and an access control list table. The ACE defines the permissions for a particular user or group, while the ACL table contains a list of all the ACEs associated with a particular resource. When a user attempts to access a resource, their credentials are checked against the ACEs in the ACL table to determine whether they are allowed or denied access.
How do ACLs Work?
To better understand how ACLs work, let’s look at an example. Imagine you have a home Wi-Fi network and want to restrict access to certain websites. To do this, you would create a list of approved websites (ACEs) and then apply this list to every device connected to your network (ACL table). Any device that tries to access a website not on the list will be denied access, while those trying to access sites on the list will be granted access.
Access Control Lists follow a similar logic, but on a much larger scale. In a corporate network, for instance, an IT administrator can create a list of permitted and restricted resources (ACEs) and then apply this list to the entire network (ACL table). This way, only authorized users can access specific resources, while unauthorized users are denied access.
Why are ACLs Important?
ACLs play a crucial role in network security by providing an additional layer of protection against unauthorized access. They help organizations control who can access their networks, systems, and applications and what actions they can perform once inside. Without proper access controls, malicious actors can gain access to sensitive data, causing significant damage to an organization’s reputation and bottom line.
Moreover, ACLs are essential for complying with various regulatory requirements, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). These regulations mandate that organizations must have measures in place to protect sensitive data, including controlling and monitoring access to it.
Types of Access Control Lists
There are several types of Access Control Lists, each designed for different use cases and scenarios. Let’s take a closer look at some of the most common types of ACLs and their characteristics.

Various types of ACLs are tailored for different scenarios and purposes
Standard ACLs
Standard ACLs are the most basic type of ACL, allowing or denying access based solely on the source IP address. They are often used to restrict traffic from specific devices or networks, making them ideal for perimeter security. For example, a standard ACL could be used to block all traffic from a particular country or region.
Characteristics of Standard ACLs
- Based on Source IP Address Only: As mentioned earlier, standard ACLs only consider the source IP address when making access decisions.
- Applied Closest to Destination: Standard ACLs are typically applied closest to the destination of the traffic, ensuring that the least amount of traffic is processed.
- Sequential Order of Rules: Standard ACLs follow a sequential order, with the first rule matching being applied and the rest being ignored.
- No Protocol or Port Selection: Since standard ACLs only consider the source IP address, they do not support filtering based on protocols or ports.
Use Cases for Standard ACLs
- Restricting Traffic at the Network Perimeter: Standard ACLs can be used to block traffic from specific countries or regions, providing an additional layer of security at the network perimeter.
- Filtering Out Unwanted Traffic: Standard ACLs can be used to filter out unwanted traffic, such as spam or malicious requests, before it reaches the destination.
- Blocking Internal Users from Accessing Certain Websites: Standard ACLs can also be used to restrict access to specific websites within an organization’s internal network.
Extended ACLs
Extended ACLs are more advanced than standard ACLs, offering a greater level of granularity in controlling access. They allow for access control decisions based on source and destination IP addresses, protocols, and ports. These Access Control Lists are more versatile and can be used in a wide range of scenarios, making them a popular choice for many organizations.
Characteristics of Extended ACLs
- Based on Source and Destination IP Addresses: Unlike standard ACLs, extended ACLs consider both the source and destination IP addresses when making access decisions.
- Support for Protocols and Ports: Extended ACLs offer the ability to filter traffic based on protocols and ports, providing a higher level of granular control.
- Applied Closest to the Source: Extended ACLs are usually applied closest to the source of traffic, ensuring that only the necessary traffic is processed.
- Sequential Order of Rules: Similar to standard Access Control Lists, extended Access Control Lists follow a sequential order, with the first rule matching being applied and the rest being ignored.
Use Cases for Extended ACLs
- Restricting Access to Sensitive Servers: Extended ACLs can be used to restrict access to critical servers by allowing only authorized users with specific IP addresses and protocols.
- Enforcing Security Policies: Extended ACLs can help enforce security policies by allowing or denying access based on user roles, groups, or departments.
- Filtering Traffic Based on Application Protocols: Extended Access Control Lists can be used to filter traffic based on application protocols, such as HTTP, FTP, or SSH.
VLAN ACLs
VLAN ACLs (VACLs) are used to control traffic within a single VLAN. They are applied on the switch interfaces and can help prevent unauthorized communication between devices within the same VLAN. VACLs are an essential security measure for organizations that use virtual local area networks (VLANs) to segment their networks.
Characteristics of VLAN ACLs
- Applied on Switch Interfaces: VACLs are applied on the switch interfaces where they can be used to filter traffic moving between different VLANs.
- Based on MAC Addresses: VACLs allow filtering of traffic using source and destination MAC addresses, providing a higher level of control over who can access resources within a VLAN.
- No Protocol or Port Selection: Similar to standard ACLs, VACLs do not support filtering based on protocols or ports.
- Allow/Deny Actions: VACLs offer the ability to specify whether traffic should be allowed or denied based on the defined rules.
Use Cases for VLAN ACLs
- Securing Network Segmentation: VACLs can be used to secure network segmentation by controlling traffic between VLANs, preventing unauthorized users from accessing resources.
- Controlling Communication Between Devices: VACLs allow organizations to control communication between devices within a VLAN, ensuring only authorized devices can communicate with each other.
- Restricting Access to Specific Services: VACLs can also be used to restrict access to specific services within a VLAN, such as file sharing or printer access.
Dynamic ACLs
Dynamic ACLs (dACLs) are similar to extended ACLs in terms of functionality, but they offer greater flexibility and scalability. Unlike traditional ACLs, which are static and must be manually updated, dACLs can dynamically update based on user roles or conditions. This makes them an ideal solution for organizations with a large number of users and a complex access control structure.
Characteristics of Dynamic ACLs
- Updated Dynamically: As the name suggests, dACLs can be updated automatically based on predefined conditions, such as user roles or network activity.
- Support for Dynamic Port Assignments: dACLs support dynamic port assignments, allowing organizations to assign specific ports to users based on their role or access needs.
- Granular Control: Similar to extended ACLs, dACLs offer granular control over traffic by allowing filtering based on source and destination IP addresses, protocols, and ports.
- Applied Closest to the Destination: dACLs are usually applied closest to the destination of the traffic, making them an efficient option for large networks.
Use Cases for Dynamic ACLs
- Role-Based Access Control: dACLs can be used to apply different access permissions to users based on their assigned roles, ensuring that they only have access to the resources required for their job.
- Guest Network Access: Organizations can use dACLs to provide guest users with limited access to the network, preventing them from accessing sensitive data or causing any security breaches.
- Device Specific Access: dACLs can also be used to restrict access to certain devices, such as printers or scanners, to prevent unauthorized use.
Time-Based ACLs
Time-based ACLs (tACLs) are a variation of traditional ACLs, where access is granted or denied based on a predefined schedule. This type of ACL can be useful for organizations that need to limit access to certain resources during specific times, such as after business hours.
Characteristics of Time-Based ACLs
- Based on Time Periods: tACLs allow for access control based on predefined time periods, such as days of the week or specific times of the day.
- Granular Control: Similar to extended ACLs, tACLs offer granular control over traffic by allowing filtering based on source and destination IP addresses, protocols, and ports.
- No Special Hardware Required: Unlike some other types of ACLs, tACLs do not require any special hardware, making them a cost-effective solution for organizations.
- Sequential Order of Rules: tACLs follow a sequential order, with the first rule matching being applied and the rest being ignored.
Use Cases for Time-Based ACLs
- Limiting Access to Sensitive Resources: tACLs can be used to restrict access to sensitive resources during certain times, such as outside of business hours.
- Controlling Bandwidth Usage: Organizations can use tACLs to limit bandwidth usage during peak hours to ensure that critical services are not affected.
- Enforcing Compliance: tACLs can also help enforce compliance by limiting access to certain data or systems during periods where it may be more vulnerable to attacks.
Best Practices for Implementing and Maintaining ACLs
Now that we have explored the various types of ACLs let’s discuss some best practices for implementing and maintaining them in your organization.
Define Your Security Policy
Before implementing ACLs, it’s crucial to define your organization’s security policy and understand what resources need protection. This will help you determine which type of ACL is best suited for your needs and what rules should be defined in your ACL tables.
When defining your security policy, be sure to consider both internal and external threats, as well as regulatory requirements. This will ensure that your ACLs are comprehensive and provide adequate protection for your network.
Keep Your ACLs Updated
As networks and applications evolve, so do security threats. It’s essential to regularly review and update your ACLs to ensure they remain effective and relevant. As part of your ongoing maintenance, consider reviewing your ACLs at least once a year to identify any new vulnerabilities or changes in your network infrastructure.
Regularly Review and Audit your ACLs
In addition to keeping your ACLs updated, it’s crucial to review and audit them regularly. This will help you identify any errors, redundancies, or conflicts that may exist in your ACL tables. It can also help you identify any unauthorized access attempts or suspicious activity on your network.
Use Standardized Naming Conventions
When creating ACLs, it’s essential to use standardized naming conventions for easy identification and management. This will help you quickly identify specific ACLs and understand their purpose, making it easier to troubleshoot and maintain them.
Optimize your ACLs for Performance
ACLs are essential for security, but they can also impact network performance if not optimized correctly. When creating your ACLs, be sure to follow best practices to ensure maximum efficiency. Some tips for optimizing your ACLs include:
- Place the most restrictive rules at the top of your ACL table.
- Use wildcard masks to cover larger ranges of IP addresses.
- Use object groups to simplify ACL configuration and management.
- Avoid using ACLs with high numbers of ACEs, as this can significantly impact performance.
Document Your ACLs
Lastly, it’s crucial to document your ACLs to have a record of what resources are allowed or denied and why. This will help you troubleshoot any issues that may arise and provide evidence of your organization’s compliance efforts.
Benefits of Access Control Lists
Now that we have explored what ACLs are and how to implement and maintain them let’s discuss the benefits they offer to organizations.
Enhanced Network Security
The primary benefit of ACLs is enhanced network security. By controlling and restricting access to resources, organizations can mitigate the risk of data breaches and unauthorized access. With proper implementation and maintenance, ACLs can prevent malicious actors from gaining access to sensitive data, reducing the likelihood of a security incident.
Organizations can reduce the risk of data breaches and unauthorized access by managing and limiting resource access effectively
Improved Compliance and Governance
ACLs are an essential part of compliance efforts for many organizations. By controlling and monitoring access to resources, ACLs help ensure that sensitive data is protected and only accessible by authorized users. This is critical for meeting regulatory requirements, such as the GDPR and HIPAA, which mandate that organizations have measures in place to protect sensitive data.
Increased Efficiency and Productivity
ACLs can also help boost productivity by preventing unauthorized users from accessing resources they do not need. By restricting access to specific resources, organizations can ensure that their network bandwidth is not wasted on unnecessary traffic. This can help improve network performance and user experience, leading to increased efficiency and productivity.
Reduced Risk of Data Breaches
Data breaches can be costly and damaging to an organization’s reputation. With ACLs in place, organizations can significantly reduce the risk of unauthorized access to sensitive data. By controlling who can access what resources, organizations can prevent data breaches and avoid the financial and reputational damage that comes with them.
Cost-Effective Solution
Implementing ACLs is a cost-effective way to enhance network security. Unlike other security measures that require significant investments in hardware and software, ACLs can be implemented using existing infrastructure, making it a budget-friendly option for many organizations.
Conclusion
Access control lists (ACLs) are a critical component of network security, providing a way to control and restrict access to resources based on user permissions. They offer a wide range of benefits to organizations, including enhanced security, improved compliance, increased productivity, and reduced risk of data breaches.
In this comprehensive guide, we have explored what ACLs are, how they work, and why they are essential. We have also discussed different types of ACLs and their characteristics, best practices for implementing and maintaining them, and the benefits they offer to organizations.
By following the best practices outlined in this guide, organizations can ensure that their ACLs are effective and provide adequate protection for their networks. With proper implementation and maintenance, ACLs can go a long way in helping organizations prevent security incidents and safeguard their sensitive data.